THORChain Core Protections: Security Architecture Validated

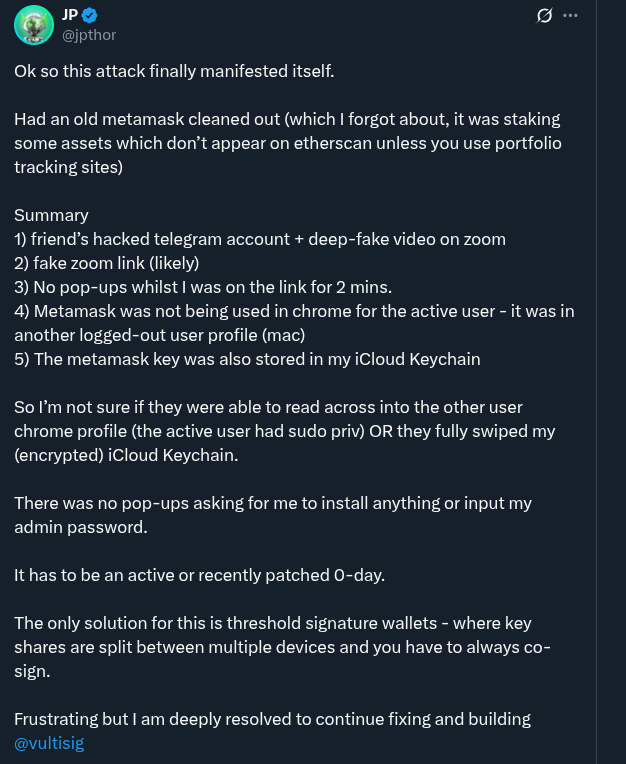
There was an incident that occurred on 9 September 2025 where private keys held by THORChain founder JP THOR were compromised. The team’s preventative security measures have successfully prevented the THORChain network from any adverse effect of the individual’s compromise.
No funds of THORChain, THORChain Treasury, or THORChain users were at risk or affected.
Since 2022, the team has worked to systematically remove any singular point of failure on the network and protect against key compromise. This is indicative of the decentralized architecture of the protocol and deliberately conducted by the team as part of Planned Obsolescence. These protections not only made the network more secure and decentralized, but also successfully protected against the exact attack vector they were designed to prevent.
This incident highlights the importance of using MPC to protect against key compromise, as well as sufficiently decentralizing the ecosystem to protect against such an attack.
Protocol Protections
Treasury funds held in MPC Wallet
The THORChain treasury funds are held on a multisig MPC wallet: Vultisig, so in the event of an individual key compromise funds from the treasury could not be stolen. The Treasury is custodied by a committee of key holders physically located in diverse geographic regions.
Treasury LP Positions locked
The THORChain treasury also seeded new liquidity pools, providing liquidity to new pairs on the network. In May 2024, the Treasury LP positions were locked in the protocol so that the single signature treasury keys could not be used to withdraw or move the LP positions. The liquidity is held by the network and can only be moved with a consensus of validators’ approval.
Relevant PR: !3562
Standby Reserve burned
At the beginning of 2023, the Standby Reserve, which was ~60m RUNE that was earmarked to be added to the network Reserve was burned. The RUNE in this wallet no longer exists as part of the supply.
Admin Mimir keys revoked
Early this year, the Admin Mimir keys were revoked. Mimir is used by the network to control constants and parameters. Admin Mimir existed from the early days of the network to be an actor that can change parameters without a consensus, to react to potential security events and also carry out operational duties. There was a whitelist of keys that could be changed by Admin Mimir. Admin Mimir decisions could always be overridden by a majority of validators.
As part of the planned obsolescence, Node Mimir was implemented, which allowed any 3 nodes to come to a consensus on “operational” parameters. Important economic parameters must still receive a consensus by 2/3 of the validators. After Mimir V2 was implemented, Admin Mimir code was removed completely from the network.
Relevant PRs: !2588 & !3177 & !3886
Other
Relevant X Posts:
- https://x.com/lookonchain/status/1966426219639144474
- https://x.com/P3b7_/status/1966426113967583603
- https://x.com/jpthor/status/1966450439437611484
- https://x.com/jpthor/status/1966440849438318937
- https://x.com/jpthor/status/1965366373682491647
Community
To keep up to date, please monitor community channels, particularly Telegram and X:
Website | Documentation | X | Telegram Community | Telegram Alerts | Community Discord | Developer Discord | Explorer | RuneScan | Reddit | Gitlab | Medium | Linktree | Thorcharts | RUNE Tools





